

You’re going to have to read every single release with breaking changes.


You’re going to have to read every single release with breaking changes.


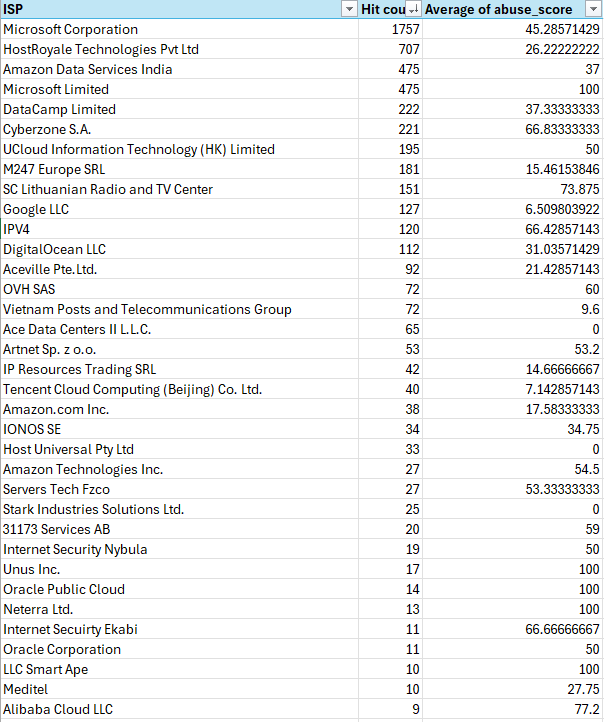
I’m trying to block the most likely attack vectors which is definitely VPS providers at this point in time. I just figure if I am blocking subnets plus additionals I identify it will force them out of these vectors to attack in ways I might be able to report better abuse.
Here check out my analysis.


No I think f2b handling it would be totally fine for me. Kids got in the way with digging around too much but will try this week.


Ahhhmazing, I’ll set this up tonight. Really appreciate the help.


I’ve used it on a machine before but given I am using a cloudflared container for ingress, can I route my traffic through a f2b container to the app? This might be ideal from a co fig perspective.
LLMs say yes but I’ll need to play around.


I have more than 50k but even that page doesn’t recommend it.
Top of that page
Recommendation: Use WAF custom rules instead
Cloudflare recommends that you create WAF custom rules instead of IP Access rules to perform IP-based or geography-based blocking (geoblocking):
- For IP-based blocking, use an IP list in the custom rule expression.
On the fail2ban front, can I run my traffic through a f2b container and out into my app?


How easy is it to configure?
My goal is to download some lists from github and generate one big ban list to feed into the WAF but the community lists of Crowdsec might negate the need.


I use namesilo for everything but my .au domains.
I’d rather not have them probing my website at all. I’m not Facebook, my data is not unlimited and free.